In the high-stakes environment of cybersecurity, a security incident is an inevitability, not a possibility. The critical difference between a contained event and a full-blown crisis hinges entirely on preparedness. A meticulously crafted security incident response checklist is the single most important tool for transforming the chaos of a breach into a structured, efficient, and decisive defense. It removes guesswork when seconds count, ensuring every action taken is precise and impactful.
- Organizations with a tested incident response plan save an average of $1.49 million per breach compared to those without one (IBM Cost of a Data Breach Report 2024).
- The average time to identify and contain a data breach is 277 days, but organizations with IR plans reduce this to 253 days (IBM 2023).
- CrowdStrike's 2024 Global Threat Report found that average adversary breakout time dropped to just 62 minutes, making speed-to-response critical.
- Only 45% of organizations have a formal, enterprise-wide incident response plan (SANS Institute 2024 IR Survey).
This guide moves beyond generic advice to provide a detailed, 10-point roundup covering the complete incident lifecycle. We will break down each phase, from proactive preparation and threat detection to system recovery and post-incident analysis. To fully grasp the non-negotiable nature of a proactive security incident response checklist, it's crucial to first understand What is Incident Response and why it is so critical for businesses. This foundational knowledge highlights why a reactive approach is no longer sufficient.
You will find actionable steps, specific role-based responsibilities, evidence preservation protocols, and communication templates that your team can implement immediately. Drawing on established frameworks from NIST and SANS, this checklist is designed to equip your organization to minimize damage, protect critical assets, and maintain stakeholder trust. Whether you are formalizing your first response plan or refining a mature one, this comprehensive listicle will serve as your blueprint for building true operational resilience against cyber threats. We will cover everything you need to act with confidence and clarity when an incident occurs.
1. Preparation and Prevention Planning
The most effective incident response is one that is prevented entirely. Preparation is the foundational phase of any robust security incident response checklist, focusing on creating a resilient environment and a well-rehearsed team before a threat materializes. This proactive stage, popularized by frameworks like the NIST Cybersecurity Framework and the SANS Institute's guidelines, aims to minimize the attack surface and ensure a rapid, coordinated response when an incident does occur.
At its core, preparation involves documenting the rules of engagement. This means creating a formal Incident Response Plan (IRP) that outlines roles, responsibilities, communication channels, and escalation paths. It's crucial to understand the difference between policy and procedures; a policy sets the "why" (e.g., "We must protect customer data"), while procedures define the "how" (e.g., "The on-call engineer will immediately isolate the affected server"). According to the Ponemon Institute, organizations in the top quartile of incident preparedness spend an average of $2.46 million less on breach-related costs than their unprepared counterparts.
"The time to fix the roof is when the sun is shining. In cybersecurity, the organizations that invest heavily in preparation and rehearsal consistently outperform those that rely on reactive measures alone. Your incident response plan should be a living document that your team can execute from muscle memory."
-- Gen. Keith Alexander, Former Director of the NSA and Commander of U.S. Cyber Command, Founder of IronNet Cybersecurity
Key Actions and Implementation
Successful preparation hinges on a few critical, ongoing activities:
- Asset and Data Inventory: You cannot protect what you do not know you have. Maintain a comprehensive inventory of all hardware, software, and data assets. Classify them based on criticality to prioritize protection and response efforts. The CIS Controls (v8) list asset inventory as Control #1 and #2--the very foundation of any security program. Gartner estimates that 30% of organizations discover previously unknown assets during their first comprehensive inventory.
- Vulnerability Management: Regularly scan for, identify, and remediate vulnerabilities across your infrastructure. This includes timely patching and establishing secure configuration baselines for all systems. According to Mandiant's M-Trends 2024 report, 38% of initial intrusions exploit known, unpatched vulnerabilities--making a disciplined patching cadence essential.
- Security Awareness Training: Conduct annual or semi-annual training for all employees. A well-informed workforce is your first line of defense against phishing, social engineering, and other common attack vectors. Proofpoint's 2024 State of the Phish report found that organizations with regular security awareness training reduce successful phishing attacks by up to 86%.
- Tabletop Exercises: Run quarterly simulated incident scenarios. These exercises test your IRP, identify gaps in your procedures, and build muscle memory for your response team, ensuring they act decisively under pressure. CISA offers free Tabletop Exercise Packages (CTEPs) designed specifically to help organizations of any size conduct these exercises.
By investing in these preparatory measures, you not only reduce the likelihood of a major incident but also drastically shorten the time from detection to resolution, minimizing potential damage and recovery costs. To stay ahead of emerging threats and refine your preventative strategies, consider using resources that help you maintain an upgraded cyber posture.
Incident Response Preparedness Checklist
Use this checklist to assess your organization's readiness. Review quarterly and update as your environment changes.
| Category | Action Item | Status | Owner | Review Date |
|---|---|---|---|---|
| Documentation | Formal IRP documented and approved by leadership | [ ] | [Name] | [Date] |
| Documentation | Role-based playbooks for top 5 incident types | [ ] | [Name] | [Date] |
| Team | IR team members identified with 24/7 contact info | [ ] | [Name] | [Date] |
| Team | Backup personnel assigned for each role | [ ] | [Name] | [Date] |
| Team | External DFIR retainer in place | [ ] | [Name] | [Date] |
| Tools | SIEM deployed and tuned with current detection rules | [ ] | [Name] | [Date] |
| Tools | EDR on all endpoints (servers, workstations, mobile) | [ ] | [Name] | [Date] |
| Tools | Forensic toolkit assembled and tested | [ ] | [Name] | [Date] |
| Communications | Out-of-band communication channel established | [ ] | [Name] | [Date] |
| Communications | Pre-drafted notification templates for all audiences | [ ] | [Name] | [Date] |
| Training | Tabletop exercise conducted in last 90 days | [ ] | [Name] | [Date] |
| Training | All-staff security awareness training completed | [ ] | [Name] | [Date] |
| Legal | Regulatory notification requirements mapped | [ ] | [Name] | [Date] |
| Legal | Cyber insurance policy reviewed and current | [ ] | [Name] | [Date] |
| Backups | Immutable backups verified and tested for restoration | [ ] | [Name] | [Date] |
Tip: Print this checklist and store it with your physical "go bag." Digital copies may be inaccessible during a serious incident.
2. Detection and Analysis
Once a potential threat bypasses preventative measures, the focus immediately shifts to identification. Detection and Analysis is the investigative phase of the security incident response checklist, where security teams work to confirm whether an alert signifies a genuine incident. This stage, central to models from Gartner and Mandiant (now part of Google Cloud), involves sifting through alerts from various tools to understand an event's scope, severity, and nature before taking action.
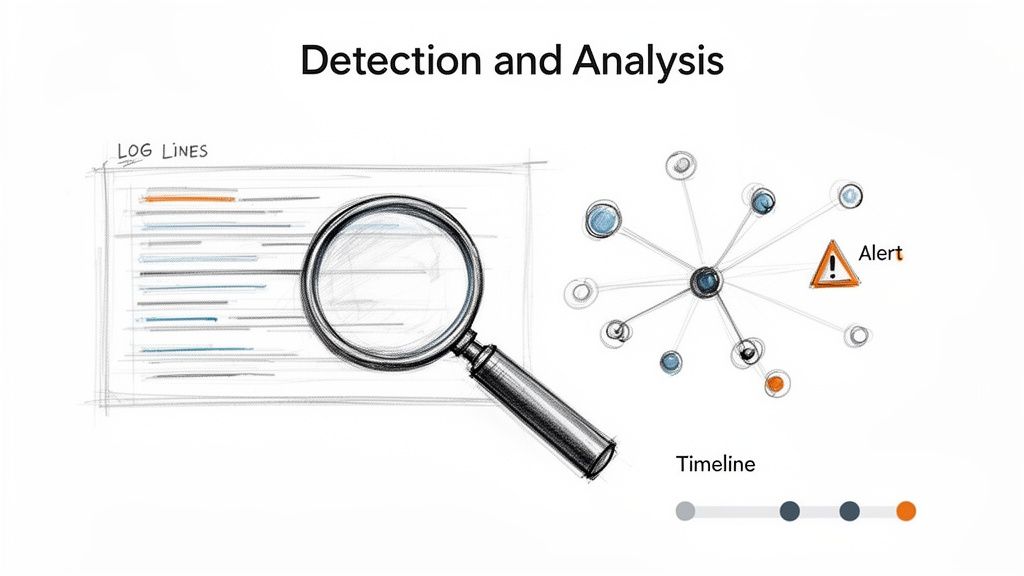
The core objective is to move from a sea of data points to a confirmed, classified incident. This involves analyzing logs, network traffic, and endpoint data to piece together the attacker's actions. For example, the initial detection of the SolarWinds supply chain attack was not a simple malware signature but an alert for anomalous login activity, which required deep analysis to uncover the sophisticated breach. Similarly, platforms like Splunk or Elastic are used to correlate events across multiple systems, turning low-fidelity alerts into a high-confidence incident notification.
The scale of the detection challenge is enormous. According to Gartner, the average enterprise SIEM processes over 10,000 events per second, yet only a fraction represent genuine threats. The key challenge is signal-to-noise ratio: a Vectra AI study found that 67% of SOC analyst time is spent investigating alerts that turn out to be false positives or benign activities.
Key Actions and Implementation
Rapid and accurate detection is built on a foundation of visibility and context:
- Establish a Behavioral Baseline: Before you can spot anomalies, you must define "normal." Use monitoring tools to profile typical network traffic, user activity, and system performance. This baseline makes deviations, like AWS GuardDuty flagging unusual API calls, stand out immediately. UEBA (User and Entity Behavior Analytics) tools can reduce false positive rates by up to 80% compared to rule-based detection alone (Gartner).
- Correlate Alerts: Modern environments generate immense alert volume. Implement SIEM (Security Information and Event Management) rules to correlate related alerts from different sources (e.g., endpoint, firewall, cloud) to reduce noise and surface true threats. Effective correlation can reduce alert volume by 90% or more, allowing analysts to focus on genuine incidents.
- Leverage Threat Intelligence: Subscribe to threat intelligence feeds. These services provide up-to-date indicators of compromise (IOCs) such as malicious IP addresses, file hashes, and domain names, enabling faster pattern matching and validation of suspicious activity. CISA's Automated Indicator Sharing (AIS) program provides free machine-readable threat intelligence to participating organizations.
- Validate and Classify: Not every alert is an incident. Establish a process for analysts to manually validate high-priority alerts. Once confirmed, classify the incident based on its type (e.g., malware, phishing, DoS) and severity to trigger the appropriate response playbook. Use the MITRE ATT&CK framework to map observed tactics and techniques, providing your team with a common language to describe attacker behavior.
By mastering detection and analysis, you ensure that your response team focuses its efforts on real threats, armed with the necessary context to act swiftly and effectively, minimizing the potential impact of an attack.
3. Containment and Isolation
Once an incident is identified, the immediate priority is to stop the bleeding. Containment is the critical phase in any security incident response checklist where responders take decisive action to prevent a threat from spreading further across the network. This stage, heavily emphasized in methodologies from Mandiant and CrowdStrike, is about limiting the scope of the damage and preventing the attacker from achieving their objectives, such as exfiltrating data or deploying ransomware.
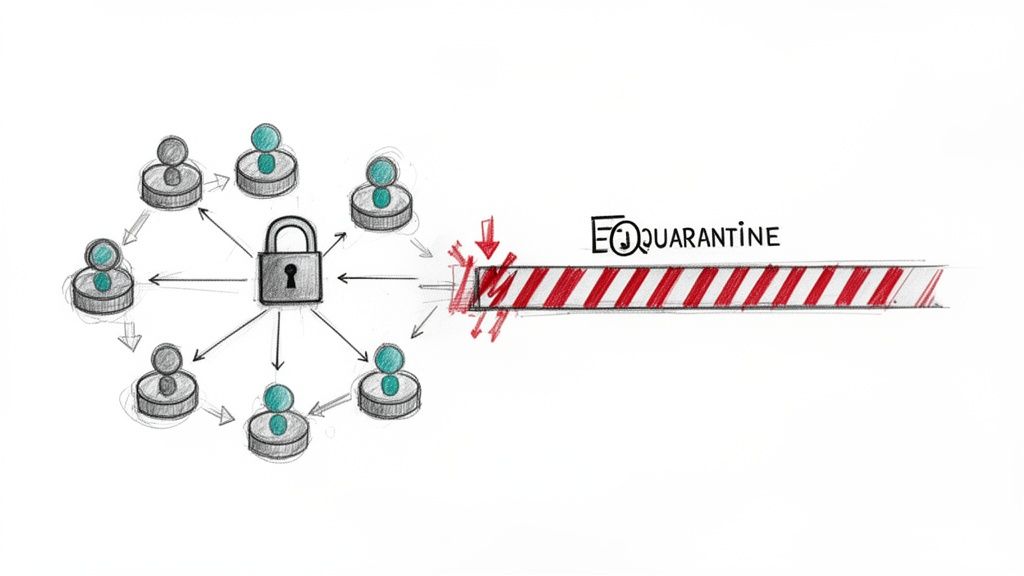
The core principle is to sever the attacker's access and mobility. This involves a two-pronged strategy: short-term containment to immediately halt the attack (e.g., disconnecting a server from the network) and a long-term strategy to implement more robust fixes (e.g., segmenting networks or deploying patches). The speed and effectiveness of containment directly influence the overall impact of the incident, as seen in cases like Microsoft's rapid response to the ProxyLogon exploit, where quick action to revoke credentials and apply patches mitigated widespread damage. IBM's research shows that breaches contained in fewer than 200 days cost an average of $1.02 million less than those that take longer.
Key Actions and Implementation
Executing a successful containment strategy requires a balance between speed and precision, ensuring actions do not corrupt crucial forensic evidence.
- Network Segmentation and Isolation: The most direct containment action is to isolate the affected systems. This can range from unplugging a network cable to using firewall rules or VLANs to logically separate a segment of the network. Modern zero-trust architectures significantly simplify this process. Organizations with microsegmentation deployed report $2.01 million in average breach cost savings (IBM).
- Credential Revocation: If credentials have been compromised, immediately disable or reset them. This includes user passwords, API keys, and SSH keys. A widespread credential reset can effectively lock an attacker out of multiple systems at once. Microsoft's response to the Midnight Blizzard attack demonstrated this at scale, revoking thousands of application secrets within hours of detection.
- Forensic Preservation: Before taking a system offline, capture a snapshot of its current state. Create memory dumps and disk images to preserve volatile data that is crucial for the subsequent investigation and eradication phases. Always use write-blockers when creating forensic images to maintain evidence integrity.
- Automated Containment Playbooks: For common threats like malware infections, use Security Orchestration, Automation, and Response (SOAR) platforms to run pre-defined playbooks. These can automatically quarantine an endpoint, block a malicious IP address at the firewall, and notify the security team, drastically reducing response time. Palo Alto Networks' Unit 42 reports that SOAR-enabled containment reduces mean time to containment by up to 80%.
By containing the threat swiftly, you reclaim control of your environment and create the necessary space to plan for eradication and recovery. For teams managing distributed assets, tools that provide secure, audited remote access are essential for executing these containment steps, and you can explore solutions for secure remote management to enhance your response capabilities.
4. Eradication and Remediation
Once an incident is contained, the next critical phase is to completely remove the threat from the environment and patch the vulnerabilities that allowed the breach. This is the core of eradication and remediation, a vital step in any security incident response checklist. This phase moves beyond temporary containment to permanently eliminate the attacker's presence and fortify defenses, ensuring they cannot exploit the same entry point again. Methodologies from NIST, SANS, and Mandiant all emphasize this step as crucial for preventing incident recurrence.
The goal is twofold: remove all malicious artifacts and fix the root cause. Eradication involves deleting malware, disabling breached user accounts, and removing any persistence mechanisms the attacker established. The MITRE ATT&CK framework documents over 200 persistence techniques that attackers commonly employ, from scheduled tasks and registry modifications to firmware implants. Remediation simultaneously addresses the underlying security weaknesses, such as unpatched software, misconfigured firewalls, or weak credentials. For instance, following the widespread Microsoft Exchange Server ProxyLogon vulnerabilities, organizations had to both remove the web shells planted by attackers and apply the emergency patches provided by Microsoft to close the door for good.
Key Actions and Implementation
Effective eradication and remediation require a methodical and thorough approach to ensure no remnants of the threat are left behind:
- Rebuild from a Known-Good State: Whenever possible, rebuild compromised systems from a trusted, clean backup or golden image created before the incident. This is often more reliable than trying to clean a live, infected system. Sophos research indicates that 70% of organizations that attempt to clean an infected system rather than rebuild experience reinfection within 30 days.
- Deploy Patches and Harden Systems: Apply all necessary security patches to affected and similar systems across the network. Implement enhanced security configurations and hardening baselines to prevent reinfection through the same or related vulnerabilities. The Center for Internet Security (CIS) Benchmarks provide free, consensus-based configuration hardening guides for virtually every major platform and application.
- Reset All Credentials: Force a reset of all passwords and credentials associated with the compromised systems, including user accounts, service accounts, and API keys. This invalidates any credentials the attacker may have stolen. Pay special attention to service accounts and machine identities, which Silverfort research shows are compromised in over 70% of advanced attacks but are often overlooked during credential resets.
- Post-Remediation Verification: After remediation, conduct extensive vulnerability scanning and penetration testing to validate that the threat has been removed and the security gaps are closed. Use integrity checking tools like Tripwire or AIDE to verify that system files are clean and unaltered. Run a full EDR scan with updated signatures across all affected systems.
5. Recovery and Restoration
Once a threat has been eradicated, the primary goal shifts to returning affected systems to normal, secure operations. This recovery phase is a critical component of any security incident response checklist, focused on restoring services, data, and business functions with minimal disruption. Guided by frameworks from the Disaster Recovery Institute (DRI) and best practices from vendors like Veeam, this stage is not just about bringing systems back online; it's about doing so safely and validating their integrity.
At its core, recovery is the execution of a pre-planned strategy to rebuild and restore. This involves carefully bringing systems back into the production environment, restoring data from clean backups, and intensely monitoring for any residual threats or signs of recurrence. The process must be methodical, following documented procedures that align with predetermined Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) to meet business continuity demands. According to Coveware, the average downtime from a ransomware attack is 24 days--organizations with tested recovery plans reduce this by up to 50%.
Key Actions and Implementation
A successful recovery is both rapid and resilient, ensuring the incident is truly over and the business can resume its mission.
- Prioritized System Restoration: Begin by restoring the most critical systems first, as defined by your Business Impact Analysis (BIA). This ensures that essential business functions are brought back online as quickly as possible, minimizing financial and operational impact.
- Validated Backup Restoration: Restore systems and data from clean, verified backups that pre-date the incident. It is crucial that these backups are isolated and have been regularly tested for integrity. Ransomware, for instance, often tries to encrypt or delete backups, making immutable snapshots a vital defense. The 3-2-1-1-0 backup rule (3 copies, 2 different media, 1 offsite, 1 immutable, 0 errors) has become the modern standard for resilient backup strategies.
- Intensive Monitoring and Validation: After restoration, closely monitor systems for any unusual activity. Validate that all security patches and configurations applied during the eradication phase are functioning correctly before re-introducing the system to the full production network. Increase logging verbosity for the first 30-60 days post-recovery to catch any signs of re-compromise.
- Phased Re-entry: Avoid a "big bang" approach. Bring systems back online in a controlled, phased manner. This allows the security team to manage the workload, monitor performance, and quickly respond if any new issues arise during the transition.
By executing a well-rehearsed recovery plan, organizations can significantly reduce downtime and ensure business continuity. To ensure your data is protected and easily restorable, you can explore robust cloud backup solutions that offer features like versioning and immutability, helping you choose the right online backup service for your needs.
6. Communication and Notification
How an organization communicates during and after an incident can be as impactful as the technical response itself. Communication and notification are the critical processes in any security incident response checklist dedicated to keeping all relevant stakeholders informed. This phase, heavily guided by frameworks like NIST SP 800-61 and regulations such as GDPR, focuses on delivering timely, accurate, and transparent information to leadership, employees, customers, regulators, and the public.
At its core, this stage is about managing perceptions and meeting legal obligations. A well-executed communication plan can preserve customer trust, demonstrate control over the situation, and prevent the spread of misinformation. Edelman's 2024 Trust Barometer found that 71% of consumers will permanently stop buying from a brand they perceive as having been dishonest about a data incident. It requires a delicate balance of transparency and prudence, ensuring that communications are factual and helpful without revealing sensitive details that could exacerbate the incident.
Key Actions and Implementation
Effective communication hinges on preparation and a clear, multi-faceted strategy that can be adapted to any incident scenario:
- Develop Pre-Approved Templates: Create communication templates for various scenarios (e.g., data breach, system outage, ransomware attack) and audiences (internal, customer, regulatory). Having these pre-drafted and approved by legal and PR teams saves critical time. The IAPP recommends maintaining templates that comply with at least your top 5 regulatory jurisdictions.
- Establish a Clear Chain of Command: Designate a single point of contact for external communications, typically from the PR or executive team. All public statements must go through a formal approval process involving legal, compliance, and leadership to ensure consistency and accuracy.
- Segment and Target Communications: Tailor messages to the specific audience. Leadership requires strategic impact summaries, IT teams need technical details, and customers need to know how they are affected and what steps they should take to protect themselves.
- Know Your Legal Obligations: Understand and document all regulatory notification requirements. For example, GDPR mandates a 72-hour notification window for certain breaches, while the SEC requires disclosure within four business days of determining materiality for public companies. As of 2024, all 50 U.S. states have their own breach notification laws with varying requirements.
By embedding a structured communication strategy into your incident response, you manage the technical crisis and its public fallout. Adhering to these principles is essential for protecting your organization's reputation and understanding the evolving landscape of data privacy and protection.
7. Forensic Investigation and Evidence Preservation
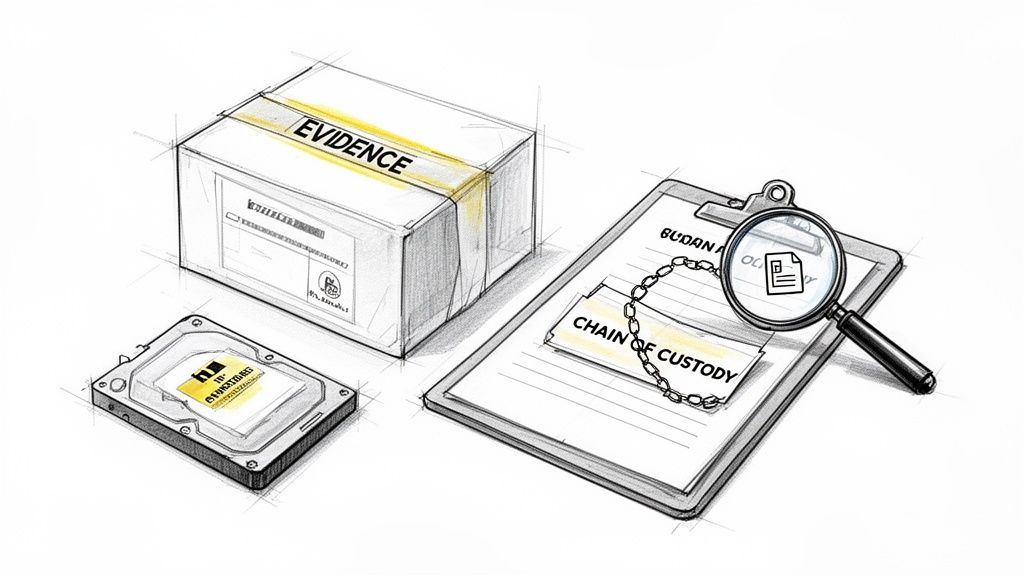
Forensic investigation is the methodical process of collecting, analyzing, and preserving digital evidence to reconstruct an incident. It is a critical component of any comprehensive security incident response checklist, moving beyond mere remediation to uncover the "who, what, when, where, and how" of a breach. This disciplined approach, championed by organizations like the SANS Forensics Institute and the FBI Cyber Division, ensures that evidence is admissible in potential legal proceedings and provides deep technical insights to prevent recurrence.
At its core, this phase is about maintaining the integrity of data from the moment of discovery. It involves creating exact copies of affected systems, analyzing volatile memory, and meticulously documenting every step to maintain a strict chain of custody. This process was famously used in high-profile cases like Mandiant's attribution of the APT1 group and the FBI's investigation into the Target data breach, where forensic evidence was key to understanding sophisticated attack vectors and attributing responsibility.
Key Actions and Implementation
Effective forensic analysis depends on a systematic and contamination-proof methodology. Rushing to restore systems without preserving evidence can destroy crucial information needed for attribution and future defense.
- Preserve Evidence Immediately: Before any remediation efforts begin, create bit-for-bit forensic images of affected drives using write-blockers to prevent accidental modification of the original evidence. Tools like FTK Imager and dd are industry standards for creating verified forensic copies. NIST SP 800-86 provides the authoritative guide for integrating forensic techniques into incident response.
- Collect Volatile Data First: Prioritize the collection of transient data like RAM content, active network connections, and running processes. This information is often lost upon system reboot and can contain critical attacker activity. The order of volatility (RFC 3227) should guide your collection priorities: registers, cache, routing table, kernel state, RAM, temp files, disk, remote logs, then physical evidence.
- Maintain Strict Chain of Custody: Document every action taken with the evidence. This includes who handled it, when, why, and how, using signed logs. This documentation is essential for the evidence to be considered legally admissible. The National Institute of Justice recommends using standardized chain of custody forms that include cryptographic hashes (MD5 and SHA-256) of all evidence files.
- Use and Document Forensic Tools: Employ reputable forensic tools and document their versions and settings for every procedure. This ensures that the analysis is repeatable and defensible. For high-impact incidents, engaging a professional digital forensics and incident response (DFIR) firm is highly recommended.
By adhering to these forensic principles, you transform a security incident from a chaotic event into an intelligence-gathering opportunity. Securely storing and transferring this sensitive evidence is also paramount; you can learn about encrypted storage solutions to maintain confidentiality during the investigation.
8. Threat Intelligence and Indicator Sharing
A security incident is rarely an isolated event; it is often part of a broader campaign targeting multiple organizations. Threat intelligence and indicator sharing is the process of transforming incident data into actionable insights and distributing them to the wider community. This collaborative defense, championed by entities like CISA and the SANS Internet Storm Center, helps other organizations proactively defend against the same attacks, turning one company's reactive response into the community's proactive defense.
At its core, this phase involves extracting Indicators of Compromise (IOCs) such as malicious IP addresses, file hashes, or domain names, and Tactics, Techniques, and Procedures (TTPs) used by the attacker. Sharing this information creates a powerful network effect, where the community collectively becomes more resilient than any single organization could be alone. For a comprehensive security incident response checklist, this step shifts focus from internal recovery to external contribution, strengthening the entire ecosystem. The Cyber Threat Alliance reports that organizations actively participating in threat intelligence sharing detect threats an average of 47% faster than those operating in isolation.
Key Actions and Implementation
Effective intelligence sharing hinges on structured analysis and responsible dissemination:
- Join Industry ISACs: Participate in an Information Sharing and Analysis Center (ISAC) relevant to your sector, such as the FS-ISAC for finance or the H-ISAC for healthcare. These provide a trusted, confidential channel for sharing highly relevant threat intelligence. There are currently over 25 sector-specific ISACs in the United States alone.
- Utilize the MITRE ATT&CK Framework: Document attacker behavior using the MITRE ATT&CK framework. This provides a common, standardized language to describe TTPs, making the intelligence you share immediately understandable and actionable for others. The framework currently catalogs over 700 techniques and sub-techniques across enterprise, mobile, and ICS environments.
- Sanitize and Share IOCs: Before sharing, sanitize all indicators to remove any sensitive or proprietary company information. Contribute these sanitized IOCs to public threat intelligence platforms like VirusTotal, AbuseIPDB, or the Cyber Threat Alliance to benefit the broader community. Use the Traffic Light Protocol (TLP) system to clearly mark the sensitivity level of shared information.
- Automate Intelligence Consumption: Integrate automated threat intelligence feeds into your security tools (SIEM, EDR, firewalls). This allows you to immediately leverage shared indicators from trusted sources to hunt for similar activity within your own network, enhancing your detection capabilities.
By institutionalizing threat intelligence sharing, your organization not only helps protect its peers but also gains access to a wealth of external data. This crowdsourced visibility, as seen in the community response to the SolarWinds and Emotet takedown events, is critical for identifying and defending against sophisticated, widespread cyber threats.
5 Common Mistakes in Incident Response Execution
- Destroying forensic evidence by rebooting or reimaging systems too quickly. In the rush to "fix things," teams often reimage compromised servers before capturing memory dumps or disk images. Volatile data (RAM, active connections, running processes) is permanently lost on reboot. According to SANS, over 40% of organizations fail to properly preserve volatile evidence during their first major incident.
- Using compromised communication channels during the response. If attackers have access to your email or Slack, they can read your response strategy in real-time. CrowdStrike found that 23% of ransomware incidents specifically targeted communication infrastructure. Always establish out-of-band channels (Signal, personal phones, dedicated incident hotline) before you need them.
- Failing to reset service accounts and machine identities. Most credential reset procedures focus on user accounts but overlook service accounts, API keys, and machine certificates. Silverfort research shows that over 70% of advanced attacks leverage service accounts, which often have broad access and no MFA. A partial credential reset gives attackers a way back in.
- Applying the same playbook to every incident type. A ransomware attack requires fundamentally different response actions than a SQL injection or an insider threat. Organizations using generic, one-size-fits-all response procedures take an average of 38% longer to contain incidents (Ponemon Institute). Develop specific playbooks for your top 5-7 most likely incident scenarios.
- Declaring the incident "closed" without verifying eradication. Just because the immediate symptoms have stopped doesn't mean the attacker is gone. Mandiant's M-Trends report shows that 24% of breached organizations experience a second compromise from the same threat actor within 12 months--often because persistence mechanisms were not fully removed. Always conduct a thorough sweep and extended monitoring period before closing an incident.
9. Post-Incident Review and Lessons Learned
The final and most crucial stage of the cycle is not recovery, but learning. A Post-Incident Review, often called a post-mortem, is the comprehensive analysis of the entire incident response process. This critical learning step ensures continuous improvement and is a cornerstone of a mature security incident response checklist. This phase, heavily influenced by Google's blameless post-mortem culture and formalized in frameworks like NIST SP 800-61, transforms a reactive event into a proactive opportunity to strengthen defenses.
The core principle is to dissect what worked well, what failed, and what changes are needed to prevent recurrence or improve future responses. The goal is not to assign blame but to identify systemic weaknesses in technology, processes, or training. A well-executed review provides a roadmap for enhancing security controls, updating playbooks, and refining the entire incident response plan, ultimately reducing future risk and impact. The Ponemon Institute found that organizations conducting thorough post-incident reviews reduce the cost of subsequent breaches by an average of $280,000.
Key Actions and Implementation
An effective lessons learned process is structured, timely, and action-oriented:






